In 2014, I was having a look at the Mozilla Firefox OS Sync App (https://marketplace.firefox.com/app/pcsync). This App allows to sync your Firefox OS phone to your Firefox browser on your PC.
While I was trying it out I noticed a major security flaw with the way the App on the phone and the plugin within Firefox Browser communicate together over WI-FI, which exposes all data stored on the phone, i.e. contacts, photos, videos etc.
What is worse, is that in most scenerios the phone user does not close the phone sync application and leaves it running in the background, unaware that there is a giant hole, right in his/her pocket when someone accesses his/her data silently.
The security issue here is due to the simplistic approach of how it was designed.
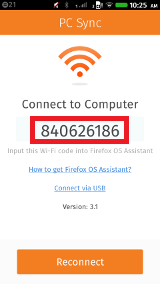
The code you see highlighted in the screenshot is simple the IP converted in to a more user friendly code. This code is then inputted in to the plugin on the Firefox browser, which then communicates to the phone via WIFI, for it to work the phone and PC will have to be on the same network.
We have created a small exploit which will dump the contacts of any phone that is found vulnerable and will not trigger the phone notification that someone is connected to the phone.
The exploit works by pinging all IP address ranges on that network against the hard coded port (Port: 25679) in the App and wait for the app to reply with an acknowledgment packet. Once that acknowledgment packet has be received the attacking application, can then send the required commands to dump any of the information from the phone.
The source code for this exploit tool is available here:
https://github.com/lookuga/FireFoxOSRemoteInformationDumpSyncExploit




