The article was written by Matthew Anthony Pace and was published on the Sunday Times Tech-Sunday (15 November 2015)
More and more websites are pushing for responsiveness, which means a much wider audience can use a website across multiple devices and platforms. While packaged web apps are essential a responsive website encapsulated to look like a normal native application that runs outside the web browser. Packaged web apps will usually have more freedom to access device APIs not available normally available to websites.
The technology being made available to packaged web apps currently depends entirely on the manufacture of platform and the operating system on which the packaged web app runs upon.
Most of the technology APIs being made available to developers are first created by leading web browser creators such as Mozilla, Google or Microsoft, in some cases they will work together to push a new technology APIs forward. After sometime working on the new API and being stable enough, a draft document it presented to W3C to become a standardized API. This is done so that websites and packaged web apps using any technology API can be 100% cross platform compatible, which makes it easier for developers to cater their website and packaged web apps to a much larger audience. Such technology APIs include Geo-location, Push notifications and Raw TCP Sockets.
There are a number of operating systems and devices that support packaged web apps as one of the ways for 3rd party developers to create apps. One of these operating systems is Firefox OS, which is currently being pushed by Mozilla to phones, tablets and Televisions. Other operating systems that are pushing for the packaged web app standard are Chrome OS, Tizen and Alibaba's Yun.
For other operating systems that do not directly support packaged web apps out of the box such as Android and iOS, developers can use what is called a web app wrapper, which are basically minimalistic web browser with additional exposed proprietary APIs which allow access to the devices hardware such as the GPS and vibrate functions, in most cases these wrappers do not follow the W3C standards and will require developers to learn and to switch any existing code to work with the custom wrapper APIs provided by the wrapper's creator. Mozilla has also ventured in to allowing all users of Firefox for desktop, to run packaged web apps directly as native Windows or Mac Applications.
One of the most popular open source web app wrappers is called Apache Cordova which was formerly known as PhoneGap. This should not be confused with Adobe PhoneGap which is a cloud service which uses Apache Cordova in their backend. Adobe PhoneGap allows developers to create packaged web apps without purchasing the hardware required, such as requiring a Mac for developing on iPhone as the builds for the iPhone are done entirely in the cloud.
Benefits can be seen by developers using both offline and online service based packaged web apps for their main frontend. These benefits include quicker time to market as it is almost identical to website development, using the same technologies such as HTML5, JavaScript, CSS3 and even webGL for those who are developing games and other graphical apps.
A high number of high profiled development companies are already using packaged web apps as a way to bring their content to multiple device, one such company is the Russian based ZeptoLab which produced the Cut the Rope game.
Though using packaged web apps might be compelling to use, there are a few shortcomings which all developers should take into consideration.
The first would be performance, while in most cases fastest and optimized executions are not a biggest factor for more smaller simplistic apps, it is however mandatory for graphical and memory intensive apps. Though packaged web apps do come close to the performance of other lower level languages such as C using AsmJS which allows the use of lower level programming structures to be used, it will require a developer to use partially complex programming methods which he or she may not be aware of or use to.
Another issue of using packaged web apps is security, in the terms of how relatively easy it is to reverse engineer back the source code from an obfuscated code compared to other programming languages. The best way to mitigate this issue would to put any sensitive logic on a backend server away from any prying eyes.
Original Times of Malta Online Article:
http://www.timesofmalta.com/articles/view/20151115/technology/Open-the-wrapper
Copy of printed Newspaper:
We just wanted to thank everybody from around the world who downloaded Net Tools!
When we first created Net Tools, we created it more for testing the capabilities of both Firefox OS and AppControl and a learning experience in general, but we were astonished when we checked the installation report, it listed that in less than 30 days there were over 500+ installs!
So once again thank you to all of you for installing and using it, and remember to follow us on social media to stay up to date of any updates and new stuff being launched.
Also if you haven’t already installed it, please go ahead and give it a try and give it a review and star rating.

Over the last few months, we have been working on LookugA Net Tools for Firefox OS. Net Tools is for penetration and security testing and was created to give Firefox OS and its Marketplace a bit of a push in Malta.
Net Tools has the following features:
IP Address Viewer - By default the Firefox OS does not have a place to view your assigned IP address. With Net Tools you can see both your local LAN IP Addresses and you public WAN IP addresses.
Port Scanner - Allows you to scan for open ports either on a single IP address or a range of them within a local network and on the Internet.
Page Keyword Locator - Allows you to scan a range of IP addresses on a single or a number of HTTP / HTTPS port numbers for a number of specified keywords. This is useful for finding hidden web services, unsecure login pages and other web pages that could be hidden and of great interest.
The App was uploaded to the Marketplace on the 7th of September (at 11.56 PM) and was approved on the 13th of September, while the average time it takes for an App to be approved is usually 8 - 10 days depending on the queue. Network Tools was approved in 5 Days, which was relatively fast since we were 98 in the queue position.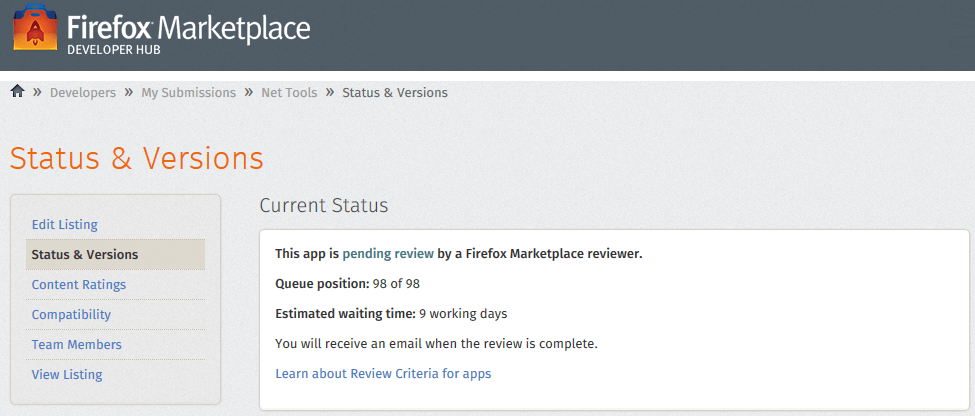
As this is still the first version, I will probably add some new items as time goes on. Some of these items are Advertisements, storing of custom values added by user and Reverse IP Look up.
The app is testing and using AceWind AppControl which will be launched sometime in the future. AppControl has a number of features such application remote management, messaging, exception handler, obfuscator and a powerful analytic and reporting engine.
Go ahead and download Net Tools from here:
https://marketplace.firefox.com/app/nettools
Additional Update:
After 48 hours being on the Firefox Marketplace a total of 90 users from around the world are using it, the analytics were captured and reported via AppControl.
As a house warming gift, we (my awesome girlfriend and I) received a Krups Piccolo Pod Coffee machine. After a couple of months the machine decided to die on us while making our nightly hot drink before bed. The problem was that the pump was no longer working.
Being naturally curious as to how things work, we decided to take a look at the inners of this little machine to see how exactly it works and perhaps fix it if we had any matching replacement parts on hand in my “electronic junk box”.

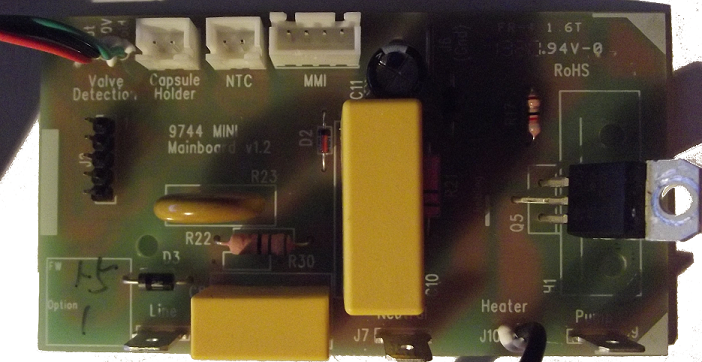
After a while investigating and tracing all the parts that are on the main board, we produced the below lists
Other items/Info:
While the above list is not a complete component list, it gives you an overview of how few components are required to build a working board, even if the power supply is unsafe and designed in a way that is not isolated from the main power grid.
After testing all the usual suspects of as to why the pump was not working, it was traced back to the mainboard generic microcontroller IC (which is on the underside of the PCB).

Now with all the power of google on our side, I was unable to find much information about this IC. The only information I was able to find with regards to the IC and the machine itself is the below. Which either means the IC is a custom designed one or it relabeled from some other manufacture. Either way, fixing/replacing this IC was going to be next to impossible.
http://www.helbling.ch/htk-en/project-examples/kaffeemaschine-piccolo-1
http://www.mikrocontroller.net/topic/211586
Check back soon for part 2 for a complete tear down tutorial of the Krups Piccolo and part 3 which we replace the stock mainboard with an open source one that has more features that anyone can build.
The article was written by Matthew Anthony Pace and was published on the Sunday Times Tech-Sunday (21st June 2015)
In today’s world over 70 per cent of internet traffic is run and used by autonomous robots and automated systems. Out of that traffic, over 80 per cent is for malicious purposes.
Mind you, automation carries various benefits. Automated systems are developed to perform repetitive and trivial tasks that would be inefficient and take a great deal longer for humans to do. While some automated systems can be developed to learn by themselves to be able to handle future events and tasks which may not have been catered for during development, in most cases they are built to perform the same action or task over and over again.
Highly advanced automated systems do exist, which can perform complex solutions to problems such as ones related to visual and audio recognition and manipulation. While these systems may perform well, they are still not capable enough to replace a human being yet.
Other bots are employed for malicious uses, ranging from simple denial-of-service attacks to social media fraud and gambling, including placing bets and providing an unfair advantage in online multiplayer video games.
Leading social media sites are under constant bot threat. Bots are used to create large amounts of fake user profiles, which are then used to provide likes, followers and written reviews to people willing to pay for them. While this does not directly affect legitimate content users, it provides false popularity. A large amount of social media content has gone viral this way, as certain social media sites use popularity algorithms to place the most popular content on the platform’s home page.
In recent years the use of bots in the online gaming sector has been on the rise. Although some gaming companies are against bots, others have welcomed the use of bots with open arms and even offer a direct application programming interface to make it easier for automated developers to integrate with. This also gives gaming companies more transparency over who, what and how often the bots are performing actions – in turn, this allows operators to put in place limits and thresholds for each account accessing the application programming interface, in order to prevent abuse.
The most common malicious purpose for bots is in botnets. These are large-scale distributed systems which are under control through a single user or a group of users with an intent to use a large amount of computing resources. Botnets can be used for distributed denial of service attacks, large-scale complex calculations such as password hashing which helps the cracking of passwords faster, and even for mining Bitcoins. These bots are usually packaged with legitimate free software to encourage users to download and install them – the user is of course completely unaware of the additional installation.
In the online multiplayer video gaming community, there has always been a market for software that provides unfair advantages against legitimate gamers. Such applications include aimbots which, as the name suggests, provide auto aiming and auto firing capabilities. There are also resource miners which are mainly used in role-playing games that require resources to level up and complete the game.
When it comes to detecting and defending against malicious bots, it can be as simple as implementing a Captcha system on the software that requires protection against abuse. A Captcha system is used to confirm that a request has originated from a human user. While this is a good starting point to prevent automated requests, it should be used in conjunction with denial-of service protection and originating country, IP address and proxy checks against a known global blacklist.
For gaming, preventive measures include the implementation of a pathway and event logging system which tracks the movement and events that are triggered by the gamer. These logs are then reviewed for any repetitiveness or erratic behaviour. Another concept which is used widely in MMORPGs is random game events. These are in game events that occur at random intervals and which are not a normal part of gameplay. For instance, this could be the blocking of a main pathway in the quest, which would require the player to manually find a new pathway. This can cause an unintelligent bot to start behaving erratically as it would not know how to handle the event. Once detected by the mentioned systems, an appropriate disciplinary action can be taken against the offending gamer.
Original Times of Malta Online Article:
http://www.timesofmalta.com/articles/view/20150621/technology/The-rise-of-the-bot-army
Copy of printed Newspaper: